What is Linux?
Linux is a free and open-source operating system. It's also one of the most popular operating systems in use today, with millions of users worldwide.
Linux was created by Linus Torvalds in 1991 and has since grown into an enormous community of developers who contribute code to improve its performance, stability and usability. The Linux kernel itself is licensed under the GNU General Public License (GPL), which means that anyone can modify it as long as they release their modified version under the same license
The Architecture of Linux
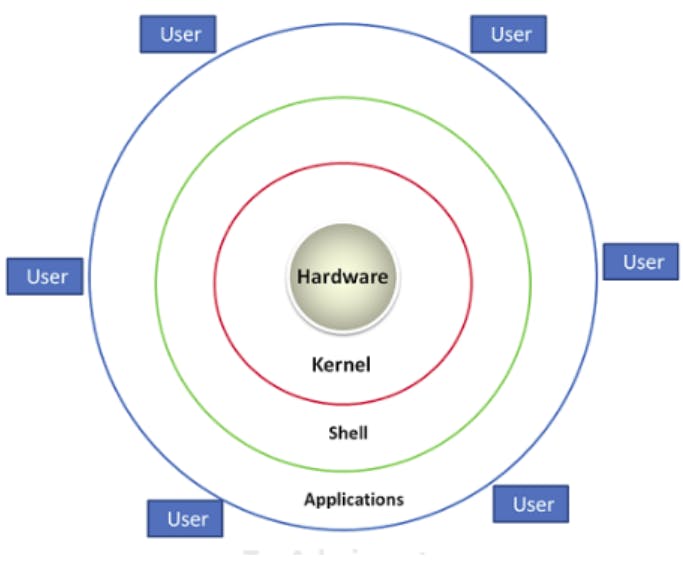
Linux is an open-source operating system that is built upon the Unix operating system. The Linux architecture is composed of four main components: hardware, kernel, shell, and applications.
Hardware: This is the physical component of a computer system, which includes the CPU, memory, storage devices, input/output devices, and other peripheral devices.
Kernel: The kernel is the core of the Linux operating system. It acts as an interface between the hardware and software components of the system. The kernel is responsible for managing the system resources, such as memory, CPU, and input/output devices. It also provides the system call interface that allows applications to interact with the operating system.
Shell: The shell is the user interface that allows users to interact with the operating system. It provides a command-line interface that allows users to run commands, execute programs, and manage files and directories. The shell also provides scripting capabilities that allow users to automate repetitive tasks.
Applications: The applications are the software programs that run on top of the operating system. They include web browsers, text editors, media players, and other software tools that allow users to perform various tasks on their computers.
In summary, the Linux architecture is a layered system consisting of hardware, kernel, shell, and applications. The kernel acts as the core of the operating system, while the shell provides a user interface for interacting with the system. Applications run on top of the operating system and allow users to perform various tasks on their computers.
Benefits of Linux
Stability and reliability: Linux is known for its stability and reliability, making it a popular choice for servers and other mission-critical applications. It can run for extended periods of time without crashing or needing to be rebooted.
Flexibility and customization: Linux is highly flexible and customizable, allowing users to modify the operating system to fit their specific needs. Users have access to a wide range of software and configuration options to create a personalized computing experience.
Security: Linux is inherently more secure than other operating systems due to its open-source nature. The code is open for anyone to view and audit, which makes it easier to identify and fix security vulnerabilities. Additionally, Linux's permission-based system allows users to control access to files and applications, which can prevent unauthorized access and improve security.
Open-source community support: Linux has a large and active open-source community that provides support, resources, and development for the operating system. This community-driven approach results in faster updates and bug fixes, as well as a wealth of documentation and tutorials.
Compatibility: Linux is highly compatible with a wide range of hardware and software. It can run on older hardware and has support for a variety of programming languages, databases, and development tools. This makes it a popular choice for developers and businesses that need a flexible and compatible operating system.
Linux Distributions (Flavours of Linux)
Linux distributions are operating systems that can be installed on your computer. There are numerous Linux distributions available, but we will concentrate on the most popular ones:
Ubuntu:
- User-friendly distribution based on Debian
- Known for ease of use and extensive community support
- Popular among beginners
- Offers a variety of desktop environments
Debian:
- Stable and reliable distribution
- Extensive package repository
- Commitment to free software
- Often used as a base for other distributions, including Ubuntu
Fedora (Red Hat):
- Cutting-edge distribution sponsored by Red Hat
- Focuses on latest technologies and innovations
- Often used by developers
- Serves as upstream for Red Hat Enterprise Linux (RHEL)
Arch Linux:
- Lightweight and flexible distribution
- Allows users to build their system from scratch
- Choose only the packages they need
- Follows a rolling release model for latest software
openSUSE:
- Versatile distribution
- Offers stability and innovation through Leap and Tumbleweed releases
- Known for powerful configuration tool, YaST
- Commitment to the open-source community
Package Management
Package management is the process of installing, upgrading, configuring and removing software packages. Package managers typically handle dependencies automatically and can be used to install multiple packages at once.
Linux has several different package managers:
APT (Advanced Package Tool) is a command line tool that handles Debian-based systems such as Ubuntu and Linux Mint. It's similar to Yum in functionality but has fewer features than RPM or Pacman.
Yum is another command line tool that handles Red Hat-based systems like Fedora or CentOS. It's similar to Apt but has more features Apt does not handle dependency resolution by default so you'll need to use additional tools such as yum-utils or DNF (Dandified YUM).
RPM (Red Hat Package Manager) is a third-party application that allows you to install software packages on Red Hat Enterprise Linux machines without having root privileges on your computer!
Linux Security
Linux security encompasses user authentication, firewall protection, file permissions, and encryption.
User Authentication:
- Necessary for system file changes or software package installations - Root or administrative account required
Firewall:
- Blocks unauthorized access from external networks - Regulates traffic between networks using routers or gateways
File Permissions:
- Three types: read (r), write (w), and execute (x) - Access denied without appropriate permissions
Encryption:
- Safeguards data for authorized users only - Thwarts hackers from accessing sensitive information
